Hello etechnews today Welcome to this Tech Resources update from The Register
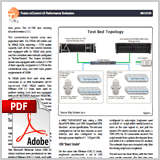 | Conventional hybrid storage solutions use NVRAM to cache data before writing to disk, then augment performance with an SSD read cache. While such solutions generally offer acceptable performance for small datasets, they are ultimately limited by the configuration and number of SSDs that can be deployed. In contrast, a hybrid storage approach can leverage PCIe-based flash to provide better performance. This not only provides direct access to block-level storage and fast read/write caching, but also allows for greater disk capacity per array shelf. Tolly evaluates the performance of a hybrid storage approach against conventional NVRAM+SSD+Disk Architecture to find that a hybrid storage solution offers up to 700% better performance in block level access tests. Download Now |
 | Kaspersky Lab’s Global IT Risks survey, conducted by research consultancy B2B International, is now in its third year. This survey speaks to IT professionals across the world, looking to understand their attitudes, opinions and beliefs about IT security and its impact on their organisation. By doing this, we hope to establish a global benchmark for the industry, to help businesses of all sizes and types gain a broader perspective of IT security thinking. Download Now |
 | In the past few years, the world of online advertising has dramatically changed. New features and targeting tactics are constantly being created and the number of players in the space continues to grow. Media buying platforms, ad exchanges, demand-side platforms (DSPs), and data aggregators are just a few of the different types of companies that have their hands in online ads. These technology companies collectively address the delivery, display, targeting and control of online advertising. Implementing the tactics laid out in this whitepaper can help reduce your overall advertising network latency. Being able to provide a seamless service to your clients will boost their confidence in your advertsing network and help you build long-lasting relationships that, along with reducing latency, have the potential to increase revenue. Download Now |
 | Before you can plan to recover your infrastructure you need to understand what you have and what you need to protect. This Disaster Recovery Self-Assessment walks your team through the process to determine the financial risk for each of your applications. The self-assessment starts by walking you through the three most common threats to business infrastructure using a flowchart. Then you will assess the financial vulnerability of your applications based on single-day outages, multi-day outages and prolonged disruptions. Developed with the intention of helping you place dollar amounts on the value of protection of your application, this self-assessment will be a helpful tool when budgeting for Recovery-as-a-Service and talking to your finance team about the need to protect your applications. Download Now |
|
Terms and Conditions
By downloading any of the papers, or by watching for any of the live or on-demand events above, you agree that your supplied personal details will be passed on to the sponsor of the paper/event, and that this organisation may contact you in the future with further information about their products and services. You can request a stop to such communications at any time.




No comments:
Post a Comment
Note: Only a member of this blog may post a comment.